I am currently trying to reverse engineer the Renkforce A460 (Thermo-/Hygrometer, https://www.conrad.de/de/thermo-hygrometer-app-basierend-renkforce-a460-1170966.html) BLE protocol, to be able to include it in pimatic as well.
This is what I found out so far:
- The device updates data every 30 seconds.
- The devices sends bursts of about 2 seconds with messages between 32 and 55 byte length.
- The app which goes with the device is able to show up to 7 different parameters: Temperature, humidity, WBGT, Humidex, Heat Index, Mold Index and Flu Index.
- I assume that those values are also transmitted in the messages.
- There are 4 types of messages I could identify so far: Pairing messages (54 byte), short messages (32 byte), medium messages (38 byte) and long messages (55 byte).
- I assume that data values are transmitted only in long messages.
- As the devices mac address is transmitted in bit-reversed order I assume the whole message is transmitted in bit-reversed order.
- You will find some more minor details in this overview.
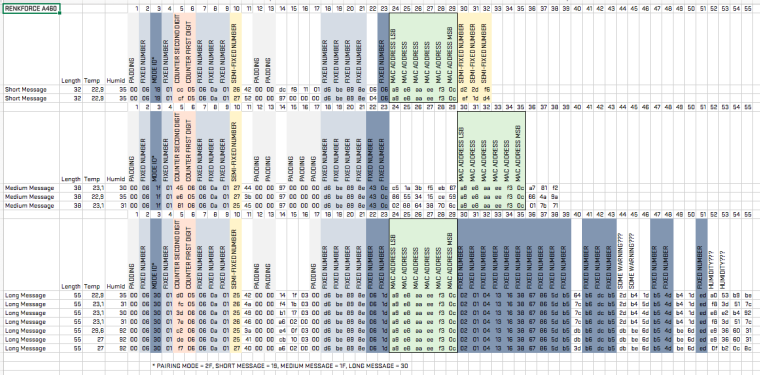
As I am mainly interested in using the temperature and humidity data I don’t care for every detail in the message. Still I wasn’t able to figure out which value corresponds to which byte.
I would be very thankful if someone could have a look at the current data. Maybe we can find out more together and solve this riddle. I would highly appreciate if some of you could just give me some methodical advice on how to approach this problem best.
If requested I can also post PCAP or CSV files with the BLE data I sniffed.
Best,
Matthias

